Over the past few years I have attended many international conferences (and even a few in Ireland). These conferences can usually be classified into two different types.
The first type of conference events are the academic type. This are usually of a non-commercial nature, and therefore they have limited budgets. However, the attendees are normally from a younger age group. So the social events at these conferences tend to be cheaper, but also more energetic.
The second type of conference events are the industry type. I have been to many of these where there are a small number of people, but big deals are done during them. It is not unusual (at least during previous better economic times) for the companies selling to spend several thousand euro per head on the social events. These social events are usually very unique opportunities that an individual would not be able to experience. They also tend to be more serious, and they are aimed at an older age group.
Earlier today I read about DomainFest 2009 in Playboy Mansion Party Announced For DomainFest. As the title suggests, the social event is going to be held in the Playboy Mansion!
I think that this is one of the most unusual social events that I have ever seen as part of a conference! It certainly would be an unforgettable experience!
Unfortunately, this conference is outside of my field :(
Tags: DomainFest, Playboy
Comments Off on Conference Social Events
I read an intriguing article yesterday that suggested that adultery facilitating websites are seeing an increase in business at the moment! The article’s author suggests that this may be due to financial employees having too much time in their lives and not enough risk!
The complete article is Adultery website lures recession-hit balding bankers.
Comments Off on Internet Growth Area During Economic Downturn
There are two articles in the news today regarding child pornography prevention measures that are being applied at national level. These articles caught my attention because I think that they are great example of how not to apply censorship!
The first article describes how six ISPs in the UK are blocking access to a Wikipedia web page that contains a photo of a naked girl in her early teens. Initially this sounds reasonable, but the block is being applied to the whole page rather than simply the photo. Furthermore, the photo is of a well known album from 1976 by a well known band. So clearly the intention of publishing this web page is not to promote child pornography.
The ISPs are implementing the block using a transparent proxy that is not forwarding the original client IP address to Wikipedia. Unfortunately, this means that Wikipedia cannot identify individual clients within these ISPs, so all users of these ISPs are now blocked from updating Wikipedia!
To add to the stupidity of this situation, the photo is widely available on the Internet already, and a simple search for “virgin killer” on Google Images finds it. Apparently many UK bloggers are now posting the image in protest.
For more details about this see Brit ISPs censor Wikipedia over ‘child porn’ album cover.
I am delighted to report that my ISP (Eircom) is not blocking access to this web page! I hope it stays this way. If you want to test your ISP then simply try viewing Virgin Killer.
The second article describes how an Australian judge recently found a man guilty of possessing child pornography. The child pornography was a fake Simpsons cartoon that depicted some of the characters have sex. For more details about this see Fake Simpsons cartoon ‘is porn’.
Again, this seems like excessive policing to me.
Tags: Censorship, Eircom, Google, ISP, Pornography, UK, Wikipedia
Comments Off on Extreme Child Pornography Prevention Measures
There was mainstream media coverage during the week about a report by Epitiro into broadband services in Ireland. The main finding was that the average fixed line consumer receives only 60% of the advertised bandwidth of his/her product.
This seems like very poor performance to me, so I decided to test my home broadband using Irish ISP Speed Test. I am an Eircom customer, and I am supposed to have a download speed of up to 3Mbps and an upload speed of up to 384kbps.
I conducted the first test very late at night time during the week, so I expected the results to be a best case scenario. This is what I got:
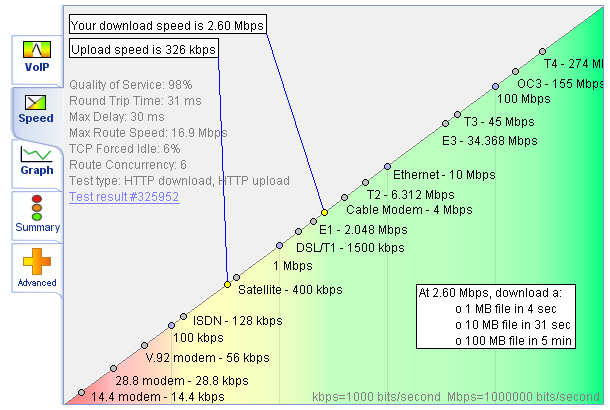
Broadband Speed Test at Night
I conducted the second test in the middle of the afternoon during the week, so I expected the results to be a worst case scenario. This is what I got:
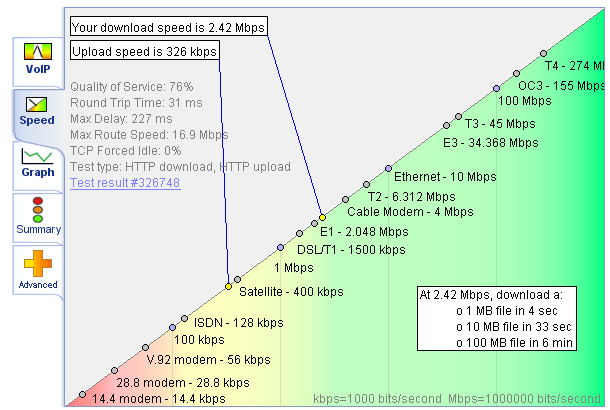
Broadband Speed Test in Afternoon
Based on these two tests I am getting roughly the same results in both my best case scenario and my worst case scenario. Furthermore, my real download speed and upload speed are both over 80% of the speeds that I am supposed to have. So I seem to be doing better than average!
For more details see Ireland Internet Performance Index, where you can download the full report.
Tags: Broadband, Eircom, Epitiro, Ireland, Irish ISP Speed Test
Comments Off on Broadband Performance in Ireland
I have a few email accounts on which I do not perform any spam filtering. There is no real need to, because I usually receive about five messages in them per week, and about three of these messages are usually spam. So I have a quick glance at them, and then hit the delete key.
I got one such spam email this morning. This email was promoting yet another wonder drug for men who are worried about the size of their penises. However, there was something very different about this email – it had a Christmas theme! I will not quote it here, but the general message was that certain ladies will be very happy with what Santa will be capable of giving them this year :|
It was the first time that I ever saw a Christmas themed spam email!
Tags: Email, Spam
Comments Off on Christmas Themed Spam
Traffic shaping is the practice of examining IP packets (but not the payload), and treating them differently, based on their characteristics. This usually consists of assigning packets priorities which determine how efficiently they are processed by networking equipment.
Traditionally, all packets within the network have been treated as equals. This worked fine when most traffic required only a small amount of bandwidth for a short durations, as is typical in web browsing and email exchange. So most ISPs were relatively happy to peer together, and carry each others traffic for free.
However, as the Internet has developed people are requiring and consuming greater amounts of bandwidth. Often this bandwidth is required across multiple ISPs’ networks, and ISPs and the intervening carriers, are increasingly charging based on the amount of traffic being exchanged. One of the main causes of significant bandwidth being required is P2P applications.
I read an article recently describing how a Canadian court granted the country’s largest ISP permission to apply traffic shaping on its core network. In particular, the court granted the ISP permission to traffic shape P2P traffic. This will effect both the retail customers and the smaller ISPs who buy wholesale services. The full article is Regulators back Bell Canada choking indie ISP traffic.
As far as I am aware, no Irish ISPs currently do any traffic shaping. However, I might be wrong about this!
My opinion is that traffic shaping will become increasingly necessary in the future to ensure that a minority of customers do not consume the majority of resources to the detriment of the majority of the users. However, I am very concerned about the prospect of traffic shaping being used by ISPs to prevent competitive services such as VoIP being used.
Would you be happy if you knew that your ISP was traffic shaping?
Tags: ISP, P2P, Peering, Traffic Shaping
Comments Off on ISP Traffic Shaping
I am currently reviewing which bank I should give my business to, and as part of this review I am considering getting a new credit card. Actually, I am wondering if I should get a debit card instead.
Therefore, I was very interested in reading about a new credit card that Visa is releasing. The unique thing about this new card is that when a user wants to use it then he/she enters his/her PIN into the card. So the card has a small keyboard in it, and yet it is still the same size as a normal credit card. The card then generates a unique one use code that must be used as part of the purchasing process. This ensures that user is really in possession of the card.
The vagueness of the Data Protection Act legislation covering the usage and storage of credit card details in the UK is also very interesting:
appropriate technical and organisational measures shall be taken against unauthorised or unlawful processing of personal data and against accidental loss or destruction of, or damage to, personal data
having regard to the state of technological development and the cost of implementing any measures
More details about all of this can be read in Visa’s digital credit card could raise legal stakes.
In terms of credit card security, the thing that really amazes me is that the CVV number is printed on the back of the card! This means that anybody who can get hold of a credit card (even for a few seconds) can later use the credit card for online purchases!
Tags: Credit Card, Debit Card, UK, Visa
Comments Off on New Visa Credit Card
Nokia has unveiled its latest NSeries mobile phone, the N97, at Nokia World 2008 in Barcelona, Spain. This new mobile phone certainly seems to be causing a lot of excitement!

Nokia N97
For more details see the official press release, download the data sheet, or read Nokia Announces the N97 – The Holy Grail.
I am not really a Nokia fan. I think it is because it traditionally made mobile phones (once it finished making toilet paper of course), and since I had a computer long before I had a mobile phone I found its devices weak on features.
The thing that strikes me most about this new mobile phone is that it appears very like a PDA to me! I guess the distinctions between these two types of mobile devices will continue decreasing!
Tags: Mobile Phone, N97, Nokia, PDA, Spain
Comments Off on Nokia Unveils N97
The Register is running an interesting competition to test people’s ability to distinguish camouflaged mobile phone base stations from normally occurring objects. There are 20 photos in total, and most of them are quite tricky! My answers are:
- Cellular mast
- Cellular mast
- Dead tree
- Flagless flagpoles
- Tree
- Flagless flagpole
- Unrelated microwave relay
- Lonely tree
- Suspicious black thing
- Fire alarm bell
- Cellular mast
- Cellular mast
- Ideal fixer-upper opportunity
- Cellular mast
- Cellular mast
- Unexplained post
- Cellular mast
- Dead spot
- Cellular mast
- Drainage pipes
If you feel like testing yourself, then proceed to Would you know a base station if you saw one?.
Tags: The Register
Comments Off on Camouflaged Base Stations
I spent several years (maybe even too many) working in the area of Location Based Services (LBSs). Indeed, I first started working in this area before it become the next “killer application” area! I spent my time working on both the technical enablers of LBSs, and the commercial groundwork for a start-up company. Happy memories ;)
This morning I read an article titled Location, location, location – geo-commerce is here and now. The article starts with the usual scenario describing how LBSs will revolutionise our lives by changing the way we make every decision. It also claims that now is the right time for LBSs to make an impact. Different people have been saying this for years now, so I suppose that somebody might be correct some day! Maybe I am just to cynical!
The article focuses on two Irish companies that are currently developing LBSs for mass market consumption based on mobile phone and PDA technology:
- ICAP Media has developed an “opt-in mobile-phone marketing platform” that supplies the user with discounts that can be redeemed in nearby businesses. Unfortunately, this just sounds like location aware spam to me :(
- Tagggit has developed a virtual tagging system that allows users to leave tags in specific locations. These tags can then be read by the same user at a later stage, or shared with other users who are in the same location. This seems like a commercial application of the Stick-e Note Architecture developed by University of Kent researchers in 1997!
There are many other companies also developing LBSs in Ireland.
Tags: ICAP Media, Ireland, Mobile Phone, PDA, Spam, Tagggit, University of Kent
Comments Off on Location Based Services in Ireland



